CyberLock®
Tulare and Kings County, CA
The Only CyberLock® Dealer in the Central Valley
Most Experienced Locksmiths in the Area
BSIS-Certifed Locksmiths
Hours:
Request Service
Hero Request Form
Thank you for contacting us.
We will get back to you as soon as possible
Please try again later
CyberLock® System Overview

CyberLock® is a key-centric access control system designed to increase security, accountability, and key control throughout your organization. Based on a unique design of electronic lock cylinders and programable smart keys, CyberLock® solves security problems that no other system can.
Main Benefits
Reviews
In-Store and Curbside Pickup Available
Contact Us Today
(559) 733-3333
Related Services
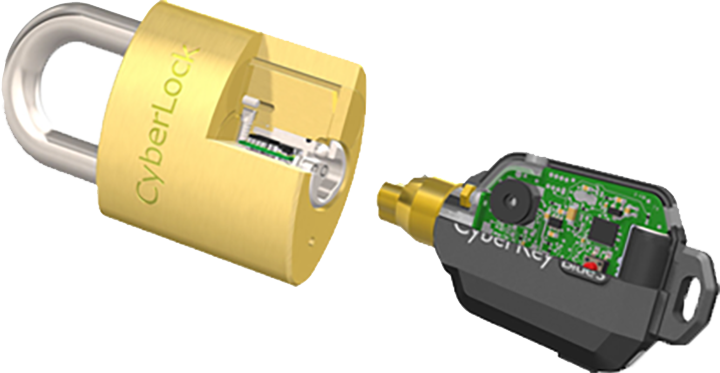
How it Works
Step 1 - Install Your High Security Locks
Replacing existing mechanical cylinders with CyberLock electronic cylinders. Each CyberLock cylinder is an electronic version of a standard mechanical lock cylinder. Installation requires no wiring, and the cylinder does not contain a battery, simply remove the existing mechanical cylinder and replace it with a CyberLock cylinder.
Step 2 - Program Your Electronic Keys
Assign CyberKey smart keys to users. CyberKey smart keys are programmed with access privileges for each user and contain a lis of locks the user may open with a schedule of days and times they are allowed access. For instance, a key can be programmed to allow access from 8am to 6pm on weekdays and 10am to 4pm on Saturdays. It can also be programmed to expire on a specific date at a specific time for increased security.
Step 3 - Open Your High Security Locks
When a CyberKey meets a CyberLock, the cylinder is energized and an information exchange occurs to determine if the key has access to that specific lock cylinder. If Authorized, the lock will open. Both the lock and key record all access events, including access granted and unauthorized access attempts.
Step 4 - Gather Your Audit Trail
When a key is presented to a communication device, the key's audit trail is downloaded and new access privileges are uploaded. Expiring keys frequently ensures users regularly update their keys. An expired key will not work until it is updated.
Step 5 - View Your Audit Trail
The CyberLock® system is managed through CyberAudit management software. Customized audit reports and periodic notifications on suspicious activities can be automatically generated via email.
"Fully stocked. Very knowledgeable service staff."
- Gail T.
serving Area
Tulare County, CA, USA
Kings County, CA, USA
Visalia, CA, USA
and surrounding areas
Business Hours
- Mon - Fri
- -
- Sat - Sun
- Closed
Contractor #636963











Share On: